Flashback:
“They are doing everything in the world to control the internet.”
– Congressman Ron Paul on the Cyber Security Act
– Law Professor: Counter Terrorism Czar Told Me There Is Going To Be An i-9/11 And An i-Patriot Act:
“Lawrence Lessig, a respected Law Professor from Stanford University told an audience at this years Fortune’s Brainstorm Tech conference in Half Moon Bay, California, that “There’s going to be an i-9/11 event” which will act as a catalyst for a radical reworking of the law pertaining to the internet.”
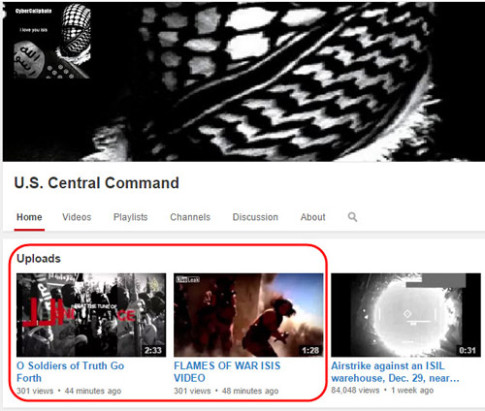
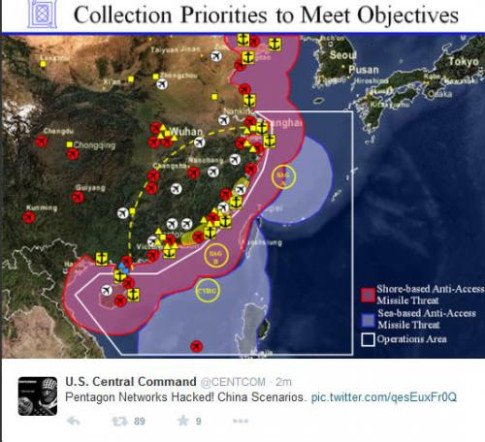
– Breaking: Jihadist Group Hacks U.S. Central Command and Is Uploading Pentagon War Game Scenarios and Personal Details of Military Members (SHFTplan, Jan 12, 2015):![]()
US Central Command (@Centcom), the unified military command responsible for security across the Arabian Peninsula and into the central Asia region, has had their Twitter account compromised. Cyber Jihadist claiming to be linked to ISIS were actively tweeting and uploading hacked war-game scenarios and other details that include phone numbers and email addresses for U.S. military personnel.
According to the hackers, the documents were obtained from a previous hack of Pentagon defense systems, as well as mobile devices owned by individuals working for or in conjunction with the military.
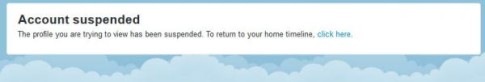
As of this writing, approximately one hour after the hack was first identified on the Centcom Twitter page, the account has been suspended and all linked data, including pictures releases of war game scenario and personal details of personnel are being wiped, presumably by U.S. National Security teams.