– Snowden on WikiLeaks Year Zero: Evidence US govt pays to keep ‘software unsafe’
* * *
PayPal: Donate in USD
PayPal: Donate in EUR
PayPal: Donate in GBP
The man who trades freedom for security does not deserve nor will he ever receive either. – Benjamin Franklin
Here is an alternative way to opt out …
Install Linux. (Maybe you have a friend, relative who knows how to do this and can teach you how to work with Linux. Learning something new is good for the brain!)
Turn off the internet connection for Windows.
Go online only with Linux.
Use all the programs you’ve got used to in Windows (while being offline).
This way you could still safely use Windows XP.
… or try to tame the beast …
– Windows 10 is spying on almost everything you do – here’s how to opt out (BGR, July 31, 2015):
Windows 10 is amazing. Windows 10 is fantastic. Windows 10 is glorious. Windows 10 is faster, smoother and more user-friendly than any Windows operating system that has come before it. Windows 10 is everything Windows 8 should have been, addressing nearly all of the major problems users had with Microsoft’s previous-generation platform in one fell swoop.
But there’s something you should know: As you read this article from your newly upgraded PC, Windows 10 is also spying on nearly everything you do.
DON’T MISS: Windows 10: The first 5 things you need to do immediately after you install it
It’s your own fault if you don’t know that Windows 10 is spying on you. That’s what people always say when users fail to read through a company’s terms of service document, right?
Read moreWindows 10 is spying on almost everything you do – here’s how to opt out
– New ‘Bash’ software bug may pose bigger threat than ‘Heartbleed’ (Reuters, Sep 24, 2014):
A newly discovered security bug in a widely used piece of Linux software, known as “Bash,” could pose a bigger threat to computer users than the “Heartbleed” bug that surfaced in April, cyber experts warned on Wednesday.
Bash is the software used to control the command prompt on many Unix computers. Hackers can exploit a bug in Bash to take complete control of a targeted system, security experts said.
Read moreNew ‘Bash’ Software Bug May Pose Bigger Threat Than ‘Heartbleed’
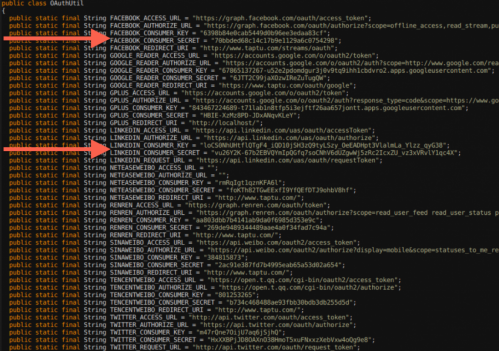
Some of the secret keys, including Facebook and LinkedIn, were discovered by PlayDrone, a tool developed by Columbia Engineering researchers that uses hacking techniques to circumvent Google security to successfully download Google Play apps and recover their sources. Credit: Columbia Engineering
– Researchers find thousands of secret keys in Android apps (Phys.org, June 18, 2014):
In a paper presented—and awarded the prestigious Ken Sevcik Outstanding Student Paper Award—at the ACM SIGMETRICS conference on June 18, Jason Nieh, professor of computer science at Columbia Engineering, and PhD candidate Nicolas Viennot reported that they have discovered a crucial security problem in Google Play, the official Android app store where millions of users of Android, the most popular mobile platform, get their apps.
“Google Play has more than one million apps and over 50 billion app downloads, but no one reviews what gets put into Google Play—anyone can get a $25 account and upload whatever they want. Very little is known about what’s there at an aggregate level,” says Nieh, who is also a member of the University’s Institute for Data Sciences and Engineering’s Cybersecurity Center. “Given the huge popularity of Google Play and the potential risks to millions of users, we thought it was important to take a close look at Google Play content.”
Read moreResearchers Find Thousands Of Secret Keys In Android Apps
– Microsoft’s secret battle against the Tor botnet (The Daily Dot, Jan 16, 2014):
In August 2013, 4 million infected computers woke up and waited instructions from their master.
The pathogen was Sefnit, a nasty bit of malware that makes infected computers mine bitcoins. Once the computers woke up, they worked under the command of Ukranian and Israeli hackers named Scorpion and Dekadent. The malware communicated with the two by downloading Tor, the powerful anonymizing software, and talking over encrypted channels. It was the first time a botnet, as a collection of slave computers is called, used Tor in such a potentially powerful way.
By using an unconventional method to exploit Windows, the hackers unwittingly forced Microsoft to show a hand few knew it had: The ability to remotely remove progams en masse from people’s computers, without them even knowing it.
– US govt caught using pirated software for military, settles for $50mn (RT, Nov 28, 2013):
The Obama administration has agreed to pay Apptricity US$50 million for pirating the company’s logistics software the US Army used beyond contracted parameters.
While the Obama administration’s has launched efforts against intellectual property theft – including the Joint Strategic Plan run by Vice President Joe Biden that aims to curb copyright infringement – the US Army was concurrently using pirated Apptricity enterprise software that manages troop and supply movements. The company sued the government, accusing the US military of willful copyright infringement.
Read moreUS Govt Caught Using Pirated Software For Military, Settles For $50 Million
– NSA infected 50,000 computer networks with malicious software (NRC, Nov 23, 2013):
The American intelligence service – NSA – infected more than 50,000 computer networks worldwide with malicious software designed to steal sensitive information. Documents provided by former NSA-employee Edward Snowden and seen by this newspaper, prove this.
A management presentation dating from 2012 explains how the NSA collects information worldwide. In addition, the presentation shows that the intelligence service uses ‘Computer Network Exploitation’ (CNE) in more than 50,000 locations. CNE is the secret infiltration of computer systems achieved by installing malware, malicious software.
– Seattle Police Deploy Crime Prediction Software City-Wide (Secrets Of The Fed, May 24, 2013):
After initial testing in two precincts, The Seattle Police Department and Mayor Mike McGinn announced last week that they will now deploy their “Predictive Policing” software to all five precincts.
The federally-funded cloud-based crime prediction software known as PREDPOL, uses mathematical algorithms similar to ones used in earthquake prediction to predict when and where a future crime is most likely to take place down to a 500-square foot area. The program combines five years’ worth of past crime data with sociological information about criminal behavior.
“We’ve had anecdotal successes with the pilot project in East and Southwest Precincts, so we’re expanding Predictive Policing citywide,” said Mayor McGinn
Read moreAND NOW: Seattle Police Deploy Crime Prediction Software City-Wide
– Write Gambling Software, Go to Prison (Wired, Dec 3, 2013):
In a criminal case sure to make programmers nervous, a software maker who licenses a program used by online casinos and bookmakers overseas is being charged with promoting gambling in New York because authorities say his software was used by others for illegal betting in that state.
New York authorities say that about $2.3 million that Robert Stuart and his company, Extension Software, received in cash and money orders for licensing his software constitutes direct proceeds of illegal, U.S.-based bookmaking operations.
“These defendants abetted large-scale illegal gambling in the U.S. and abroad,” said District Attorney Cyrus R. Vance, Jr. in a press release in October when Stuart was charged. “In doing so, they gave bettors an easy way to place illegal wagers, and created an appetite for further unlawful activity.”
But Stuart, who has been charged along with his wife and brother-in-law with one felony count for promoting gambling in New York through their software firm, says that his company sells the software only to entities outside the U.S. and that he’s not aware of anyone using it in the U.S. or using it to take illegal bets in the U.S. He also says the software doesn’t place bets, it simply provides online gambling sites with the infrastructure to select and display which sporting events they want to offer for betting and also stores the bets.
“It’s overreaching where they’re going after a software developer who sells the software with a legal license, and yet we’re still being prosecuted on how it’s being used,” Stuart says. He notes that authorities have not told him yet who exactly he’s accused of aiding and abetting.
A hearing in the case is scheduled to be held in New York on Jan. 8.
The prosecution of a commercial programmer for crimes committed by people who used his software would set a dangerous precedent for other software makers who might be held liable for how their legally licensed software is used, says Jennifer Granick, director of civil liberties for the Center for Internet and Society at Stanford University.
“It’s scary for software distributors, if someone happens to use their software for illegal activity,” she says. “If you know what people could use it for, and didn’t prevent it, did you take enough steps? What level of knowledge you need to have and all of that is not as clear as it should be [under current laws].”
– Software Meant to Fight Crime Is Used to Spy on Dissidents (New York Times, Aug 31, 2012):
Morgan Marquis-Boire works as a Google engineer and Bill Marczak is earning a Ph.D. in computer science. But this summer, the two men have been moonlighting as detectives, chasing an elusive surveillance tool from Bahrain across five continents.What they found was the widespread use of sophisticated, off-the-shelf computer espionage software by governments with questionable records on human rights. While the software is supposedly sold for use only in criminal investigations, the two came across evidence that it was being used to target political dissidents.
The software proved to be the stuff of a spy film: it can grab images of computer screens, record Skype chats, turn on cameras and microphones and log keystrokes. The two men said they discovered mobile versions of the spyware customized for all major mobile phones.
Read moreSoftware Meant To Fight Crime Is Used To Spy On Dissidents (New York Times)
– ??Stock exchange glitch cost U.S. trading firm $440m in just a few minutes and could lead to its bankruptcy (Daily Mail, Updated Aug 3, 2012):
The largest U.S. trader of equities on Wall Street, Knight Capital Group Inc was fighting for its survival on Thursday after a trading glitch wiped out $440 million of the firm’s capital, leaving it on the edge of bankruptcy.
The massive capital loss has forced the $1.5 billion firm to seek new funding as its shares plunged 70 percent in two days.
– The Kill Switch Comes to the PC (Bloomberg/Businessweek, Feb. 16, 2012):
Janne Kytömäki, a Finnish software developer, was cruising Google’s (GOOG) Android Market for smartphone apps last year when he noticed something strange. Dozens of best-selling applications suddenly listed the same wrong publisher. It was as if Stephen King’s name had vanished from the covers of his books, replaced by an unknown author. Kytömäki realized the culprit was a piece of malware that was spreading quickly, and he posted his findings online.
Google responded swiftly. It flipped a little-known kill switch, reaching into more than 250,000 infected Android smartphones and forcibly removing the malicious code. “It was sort of unreal, watching something like that unfold,” says Kytömäki, who makes dice simulator apps. Kill switches are a standard part of most smartphones, tablets, and e-readers. Google, Apple (AAPL), and Amazon (AMZN) all have the ability to reach into devices to delete illicit content or edit code without users’ permission. It’s a powerful way to stop threats that spread quickly, but it’s also a privacy and security land mine.
With the rollout of the Windows 8 operating system expected later this year, millions of desktop and laptop PCs will get kill switches for the first time. Microsoft (MSFT) hasn’t spoken publicly about its reasons for including this capability in Windows 8 beyond a cryptic warning that it might be compelled to use it for legal or security reasons. The feature was publicized in a widely cited Computerworld article in December when Microsoft posted the terms of use for its new application store, a feature in Windows 8 that will allow users to download software from a Microsoft-controlled portal. Windows smartphones, like those of its competitors, have included kill switches for several years, though software deletion “is a last resort, and it’s uncommon,” says Todd Biggs, director of product management for Windows Phone Marketplace.
Microsoft declined to answer questions about the kill switch in Windows 8 other than to say it will only be able to remove or change applications downloaded through the new app store. Any software loaded from a flash drive, DVD, or directly from the Web will remain outside Microsoft’s control. Still, the kill switch is a tool that could help Microsoft prevent mass malware infections. “For most users, the ability to remotely remove apps is a good thing,” says Charlie Miller, a researcher with the security company Accuvant.
Read moreWindows 8: ‘Millions Of Desktop And Laptop PCs Will Get Kill Switches For The First Time
– Threat from new virus-infected emails which take over your PC even if you DON’T open their attachments (Daily Mail, Feb. 2, 2012):
A new class of cyber attack is threatening PCs – emails which infect PCs without the user having to open an attachment.
The user will not even be warned this is happening – the only message that appears is ‘loading’.
The email automatically downloads malicious software into your computer from elsewhere the moment a user clicks to open it.
The mails themselves are not infected – and thus will not ‘set off’ many web-security defence packages.
Security experts say that the development is ‘particularly dangerous’.
Read moreNew Email Viruses Take Over Computers (Without Opening Any Attachments Or Links)
– Apple iTunes flaw ‘allowed government spying for 3 years’ (Telegraph, Nov. 24, 2011):
An unpatched security flaw in Apple’s iTunes software allowed intelligence agencies and police to hack into users’ computers for more than three years, it’s claimed.
A British company called Gamma International marketed hacking software to governments that exploited the vulnerability via a bogus update to iTunes, Apple’s media player, which is installed on more than 250 million machines worldwide.
The hacking software, FinFisher, is used to spy on intelligence targets’ computers. It is known to be used by British agencies and earlier this year records were discovered in abandoned offices of that showed it had been offered to Egypt’s feared secret police.
Apple was informed about the relevant flaw in iTunes in 2008, according to Brian Krebs, a security writer, but did not patch the software until earlier this month, a delay of more than three years.
“A prominent security researcher warned Apple about this dangerous vulnerability in mid-2008, yet the company waited more than 1,200 days to fix the flaw,” he said in a blog post.
Read moreApple iTunes FLAW Allowed Government Spying For 3 Years
Documents recently obtained through a Freedom of Information Act (FOIA) request reveal detailed information about the FBI’s electronic surveillance capabilities. The Electronic Frontier Foundation (EFF) filed the FOIA request in 2007 after it was reported that the agency was using “secret spyware.”
The documents show that software called the Computer and Internet Protocol Address Verifier (CIPAV) was used by the FBI since at least 2001. The software allows the FBI to collect a variety of information from a computer every time it connects to the Internet, including the IP address, Media Access Control (MAC) address, open communication ports, list of the programs running, URLs visited, and more.
It is unclear how the FBI installs the software on a computer, but it is suspected that the spyware exploits a vulnerability in the user’s browser, like other common Internet viruses.
Read moreFBI Uses Surveillance Software To Track Suspects Online
See also:
– Anti-Iran computer bug had powerful backers
– Has the West declared cyber war on Iran?

The Stuxnet computer worm has wreaked havoc in China, infecting millions of computers around the country, state media have reported.
A computer virus dubbed the world’s “first cyber superweapon” by experts and which may have been designed to attack Iran’s nuclear facilities has found a new target — China.
The Stuxnet computer worm has wreaked havoc in China, infecting millions of computers around the country, state media reported this week.
Stuxnet is feared by experts around the globe as it can break into computers that control machinery at the heart of industry, allowing an attacker to assume control of critical systems like pumps, motors, alarms and valves.
It could, technically, make factory boilers explode, destroy gas pipelines or even cause a nuclear plant to malfunction.
The virus targets control systems made by German industrial giant Siemens commonly used to manage water supplies, oil rigs, power plants and other industrial facilities.
“This malware is specially designed to sabotage plants and damage industrial systems, instead of stealing personal data,” an engineer surnamed Wang at antivirus service provider Rising International Software told the Global Times.
“Once Stuxnet successfully penetrates factory computers in China, those industries may collapse, which would damage China’s national security,” he added.
Another unnamed expert at Rising International said the attacks had so far infected more than six million individual accounts and nearly 1,000 corporate accounts around the country, the official Xinhua news agency reported.
Read moreStuxnet ‘Cyber Superweapon’ Wreaks Havoc in China, Infects Millions of Computers

President Mahmoud Ahmadinejad visits one of Iran’s nuclear plants, which have come under attack from the virus
Computers can go wrong, and everyone is used to it. But that’s at home. We assume that the machines controlling the infrastructure that makes everything tick – power stations, chemical works, water purification plants – have rock-solid defences in place to deal with unexplained crashes or virus attacks by malicious strangers.
Now, though, a new kind of online sabotage has reached its zenith with a self-replicating “worm” that started on a single USB drive and has spread rapidly through industrial computer systems around the world.
So sophisticated that many analysts believe it can only be part of a state-sponsored attack, the Stuxnet worm – or “malware” – is the first such programming creation designed with the specific intention of causing real world damage. And if the experts are right, it could herald a new chapter in the history of cyber warfare.
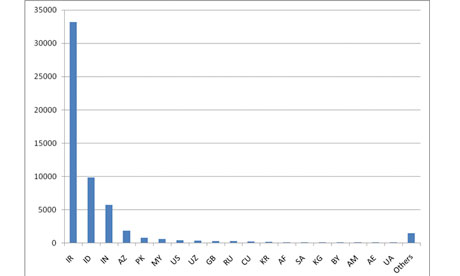
Graph shows concentration of Stuxnet-infected computers in Iran as of August. Photograph: Symantec
A powerful computer code attacking industrial facilities around the world, but mainly in Iran, was probably created by experts working for a country or a well-funded private group, according to an analysis by a leading computer security company.
The malicious code, called Stuxnet, was designed to go after several “high-value targets”, said Liam O Murchu, manager of security response operations at Symantec Corp. But both O Murchu and US government experts say there is no proof it was developed to target nuclear plants in Iran, despite recent speculation from some researchers.
Creating the malicious code required a team of as many as five to 10 highly educated and well-funded hackers. Government experts and outside analysts say they haven’t been able to determine who developed it or why.
The malware has infected as many as 45,000 computer systems around the world. Siemens AG, the company that designed the system targeted by the worm, said it has infected 15 of the industrial control plants it was apparently intended to infiltrate. It is not clear what sites were infected, but they could include water filtration, oil delivery, electrical and nuclear plants.
None of those infections has adversely affected the industrial systems, according to Siemens.
Still wonder why civilian deaths spike in Afghanistan and Pakistan?
The CIA is implicated in a court case in which it’s claimed it used an illegal, inaccurate software “hack” to direct secret assassination drones in central Asia.
The target of the court action is Netezza, the data warehousing firm that IBM bid $1.7bn for on Monday. The case raises serious questions about the conduct of Netezza executives, and the conduct of CIA’s clandestine war against senior jihadis in Afganistan and Pakistan.
The dispute surrounds a location analysis software package – “Geospatial” – developed by a small company called Intelligent Integration Systems (IISi), which like Netezza is based in Massachusetts. IISi alleges that Netezza misled the CIA by saying that it could deliver the software on its new hardware, to a tight deadline.
When the software firm then refused to rush the job, it’s claimed, Netezza illegally and hastily reverse-engineered IISi’s code to deliver a version that produced locations inaccurate by up to 13 metres. Despite knowing about the miscalculations, the CIA accepted the software, court submissions indicate.
IISi is now seeking an injunction to ban Netezza and the CIA from using the software or any derivative of it, in any context.
What could possibly go wrong?

Tom Cruise in Minority Report in which police were able to predict who was about to commit a crime
Police in America are to use Minority Report style computer programmes to predict who will commit crimes before they happen.
The software collates a range of variables then uses an algorithm to work out who is at the highest chance of offending.
In some cases it may even be able to predict where, when and how the crime will be committed.
Should trials prove a success the software could be used to help set bail amounts and suggest sentencing recommendations too.
It will be used by law enforcement agencies in Washington DC but could be rolled out nationwide if a success.
Its implementation is likely to spark an outcry from privacy campaigners and civil rights groups, not least because of the strong resemblance to the 2002 sci-fi thriller ‘Minority Report’.

Privacy concerns: Face.com has made software available that can identify people from photographs on the internet through facial recognition technology (file picture)
A software company is developing revolutionary software which provides the ability to identify people from photographs posted on the internet.
Face.com has produced technology that can identify individuals on social networking sites and online galleries by comparing their image against a known picture of them.
It means detailed profiles of individuals can be built up purely from online photographs and critics have said it could lead to exploitation by employers.
The software works be creating an algorithim of the face – a measurement of the arrangement of features including the eyes, nose and mouth.
The company says it is 90 per cent accurate when scanning typical images which appear on social networking sites.
Read moreFacial Recognition Software For Every Photograph On The Internet
Reuters has removed the article. See Google cache.
Just don’t get sick and PAY!
In case you get sick you will lose your mandatory health insurance.
It’s called ObamaCare.
(Reuters) – Shortly after they were diagnosed with breast cancer, each of the women learned that her health insurance had been canceled. There was Yenny Hsu, who lived and worked in Los Angeles. And there was Patricia Reilling, a successful art gallery owner and interior designer from Louisville, Kentucky.
Neither of these women knew about the other. But besides their similar narratives, they had something else in common: Their health insurance carriers were subsidiaries of WellPoint, which has 33.7 million policyholders — more than any other health insurance company in the United States.
The women paid their premiums on time. Before they fell ill, neither had any problems with their insurance. Initially, they believed their policies had been canceled by mistake.
They had no idea that WellPoint was using a computer algorithm that automatically targeted them and every other policyholder recently diagnosed with breast cancer. The software triggered an immediate fraud investigation, as the company searched for some pretext to drop their policies, according to government regulators and investigators.
Once the women were singled out, they say, the insurer then canceled their policies based on either erroneous or flimsy information. WellPoint declined to comment on the women’s specific cases without a signed waiver from them, citing privacy laws.
That tens of thousands of Americans lost their health insurance shortly after being diagnosed with life-threatening, expensive medical conditions has been well documented by law enforcement agencies, state regulators and a congressional committee. Insurance companies have used the practice, known as “rescission,” for years. And a congressional committee last year said WellPoint was one of the worst offenders.
But WellPoint also has specifically targeted women with breast cancer for aggressive investigation with the intent to cancel their policies, federal investigators told Reuters. The revelation is especially striking for a company whose CEO and president, Angela Braly, has earned plaudits for how her company improved the medical care and treatment of other policyholders with breast cancer.
The disclosures come to light after a recent investigation by Reuters showed that another health insurance company, Assurant Health, similarly targeted HIV-positive policyholders for rescission. That company was ordered by courts to pay millions of dollars in settlements.
In his push for the health care bill, President Barack Obama said the legislation would end such industry practices.
But many critics worry the new law will not lead to an end of these practices. Some state and federal regulators — as well as investigators, congressional staffers and academic experts — say the health care legislation lacks teeth, at least in terms of enforcement or regulatory powers to either stop or even substantially reduce rescission.
“People have this idea that someone is going to flip a switch and rescission and other bad insurance practices are going to end,” says Peter Harbage, a former health care adviser to the Clinton administration. “Insurers will find ways to undermine the protections in the new law, just as they did with the old law. Enforcement is the key.”
Microsoft on Tuesday warned that hackers are targeting a freshly-uncovered weakness in some earlier versions of its Internet Explorer (IE) Web browser software.
Microsoft said it is investigating a hole that cyber attackers are taking advantage of in IE 6 and IE 7.
“At this time, we are aware of targeted attacks attempting to use this vulnerability,” Microsoft said in an advisory posted along with a routine release of patches for Windows and Office software.
“We will continue to monitor the threat environment and update this advisory if this situation changes.”
Hackers could use the flaw to remotely seize control of computers. The new IE 8 Web browser and an old IE 5 version are not affected, according to the US software colossus.
Read moreHackers target freshly-uncovered Internet Explorer hole

A con artist convinced the CIA that he could decode secret messages sent by Al-Qaeda through Al-Jazeera broadcasts
(AFP) WASHINGTON — A con artist convinced the CIA and other US agencies in 2003 that he could decode secret messages sent by Al-Qaeda through Al-Jazeera broadcasts, Playboy magazine reported.
Duped by claims that “bar codes” on Al-Jazeera television contained targeting information for Al-Qaeda attacks, former president George W. Bush’s administration raised the terror alert and cancelled several transatlantic flights in December 2003, the report said, citing former CIA officials.
The swindler at the center of the scam was Dennis Montgomery, head of a small software company in Reno, Nevada. He persuaded the Central Intelligence Agency and the Department of Homeland Security that his technology could decipher messages with flight numbers and longitudes and latitudes meant for Al-Qaeda operatives.
With assistance from French intelligence, CIA officials eventually concluded there were no secret messages in Al-Jazeera television broadcasts, said the report, published in the magazine’s latest edition.
“A branch of the French intelligence services helped convince the Americans that the bar codes were fake,” it said.
CIA and French officials asked another technology company to find or re-create codes from Al-Jazeera transmissions and “found definitively that what Montgomery claimed was there was not,” it said.
But even after the CIA stopped cooperating with Montgomery, he succeeded in convincing other government agencies that he had valuable code-breaking technology.
In January 2009, he signed a three-million-dollar research contract with the US Air Force, according to Playboy.
Read moreReport: Swindler duped CIA and DHS over Al-Qaeda decoding scam

A little help on security from the NSA. (Robyn Beck/AFP/Getty Images)
The National Security Agency has been working with Microsoft Corp. to help improve security measures for its new Windows 7 operating system, a senior NSA official said on Tuesday.
The confirmation of the NSA’s role, which began during the development of the software, is a sign of the agency’s deepening involvement with the private sector when it comes to building defenses against cyberattacks.
“Working in partnership with Microsoft and (the Department of Defense), NSA leveraged our unique expertise and operational knowledge of system threats and vulnerabilities to enhance Microsoft’s operating system security guide without constraining the user’s ability to perform their everyday tasks,” Richard Schaeffer, the NSA’s Information Assurance Director, told the Senate Judiciary Committee in a statement prepared for a hearing held this morning in Washington. “All this was done in coordination with the product release, not months or years later in the product cycle.”
The partnership between the NSA and Microsoft is not new.
In 2007, NSA officials acknowledged working with Microsoft during the development of Windows Vista to help boost its defenses against computer viruses, worms and other attacks. In fact, the cooperation dates back to at least 2005, when the NSA and other government agencies worked with Microsoft on its Windows XP system and other programs.
The NSA, which is best known for its electronic eavesdropping operations, is charged with protecting the nation’s national security computing infrastructure from online assaults.
Read moreNSA Helping Microsoft to Improve Windows 7 Security