Stuxnet computer code designed to infect industrial plants created by well-funded hackers, says Symantec Corp expert
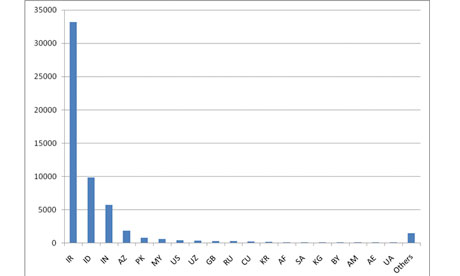
Graph shows concentration of Stuxnet-infected computers in Iran as of August. Photograph: Symantec
A powerful computer code attacking industrial facilities around the world, but mainly in Iran, was probably created by experts working for a country or a well-funded private group, according to an analysis by a leading computer security company.
The malicious code, called Stuxnet, was designed to go after several “high-value targets”, said Liam O Murchu, manager of security response operations at Symantec Corp. But both O Murchu and US government experts say there is no proof it was developed to target nuclear plants in Iran, despite recent speculation from some researchers.
Creating the malicious code required a team of as many as five to 10 highly educated and well-funded hackers. Government experts and outside analysts say they haven’t been able to determine who developed it or why.
The malware has infected as many as 45,000 computer systems around the world. Siemens AG, the company that designed the system targeted by the worm, said it has infected 15 of the industrial control plants it was apparently intended to infiltrate. It is not clear what sites were infected, but they could include water filtration, oil delivery, electrical and nuclear plants.
None of those infections has adversely affected the industrial systems, according to Siemens.
