Related info:
– Flame Virus Developed By U.S. Government
– Kaspersky At Cyber Security Conference: ‘It’s Not Cyber War, It’s Cyber Terrorism And I’m Afraid It’s Just The Beginning Of The Game … I’m Afraid It Will Be The End Of The World As We Know It’
– Obama Ordered The Stuxnet Attack On Iran’s Nuclear Facilities – And Yes: This Is An Act Of War!
– President Obama Ordered Stuxnet Attacks On Iran Nuclear Facilities
– US And Israel Created Stuxnet, Lost Control Of It
– Flame Super-Virus Threatening To Cripple Entire Nations Has ‘Hallmarks Of The NSA’
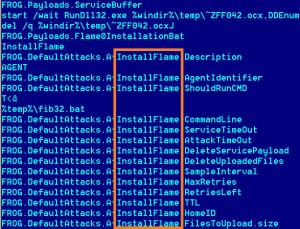
– Diving Into Flame, Researchers Find A Link To Stuxnet (threatpost, June 11, 2012):
Researchers digging through the code of the recently discovered Flame worm say they have come across a wealth of evidence that suggests Flame and the now-famous Stuxnet worm share a common origin.
Researchers from Kaspersky Lab say that a critical module that the Flame worm used to spread is identical to a module used by Stuxnet.a, an early variant of the Stuxnet worm that began circulating in 2009, more than a year before a later variant of the worm was discovered by antivirus researchers at the Belarussian firm VirusBlokAda. The claims are the most direct, to date, that link the Flame malware, which attacked Iranian oil facilities, with Stuxnet, which is believed to have targeted Iran’s uranium-enrichment facility at Natanz. If true, they suggest a widespread and multi-year campaign of offensive cyber attacks against multiple targets within that country.
According to the Kaspersky researchers, early versions of Stuxnet were, in fact, created out of components that were part of what they refer to as the “Flame platform”. But they believe development of the two malicious programs diverged after 2009, suggesting that two different development teams may have been working independently for a single entity to create malware with specific objectives, according to Kaspersky researchers, writing on the company’s blog, Securelist.
Read moreKaspersky Lab: Flame And Stuxnet Virus Share Common Origin