– The NSA’s “Boundless Informant” Collects 3 Billion Intelligence Pieces From US Computer Networks In One Month (ZeroHedge, June 8, 2013):
There’s one reason why the administration, James Clapper and the NSA should just keep their mouths shut as the PRISM-gate fallout escalates: with every incremental attempt to refute some previously unknown facet of the US Big Brother state, a new piece of previously unleaked information from the same intelligence organization now scrambling for damage control, emerges and exposes the brand new narrative as yet another lie, forcing even more lies, more retribution against sources, more journalist persecution and so on.The latest piece of news once again comes from the Guardian’s Glenn Greenwald who this time exposes the NSA’s datamining tool “Boundless Informant” which according to leaked documents collected 97 billion pieces of intelligence from computer networks worldwide in March 2013 alone, and “3 billion pieces of intelligence from US computer networks over a 30-day period.”
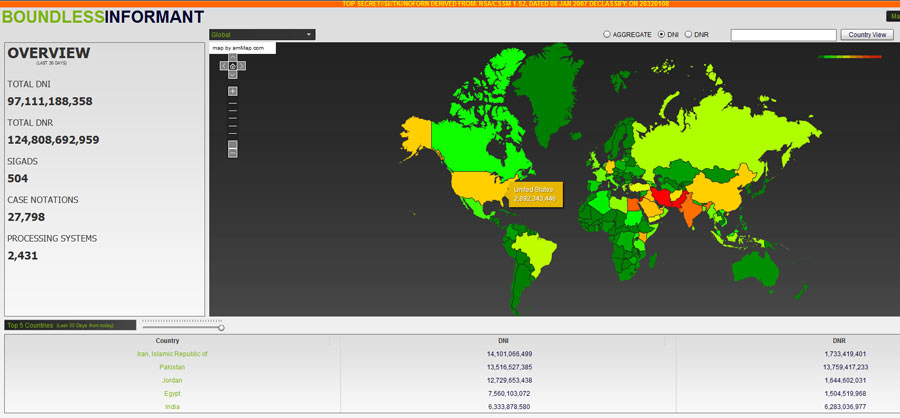
This is summarized in the chart below which shows that only the middle east has more active NSA-espionage than the US. Also, Obama may not want to show Xi the activity heatmap for China, or else the whole “China is hacking us” script may promptly fall apart.
Using simple, non-AES 256 breaking math, 3 billion per month amounts to some 100 million intrusions into the US per day, or looked at from another perspective, just a little more than the “zero” which James Clapper vouched announced earlier today is the applicable number of US citizens falling under the NSA’s espionage mandate: “Section 702 cannot be used to intentionally target any U.S. citizen, or any other U.S. person, or to intentionally target any person known to be in the United States.” Oops.
But it gets worse for the NSA. As the Guardian reports, “Emmel, the NSA spokeswoman, told the Guardian: “Current technology simply does not permit us to positively identify all of the persons or locations associated with a given communication (for example, it may be possible to say with certainty that a communication traversed a particular path within the internet. It is harder to know the ultimate source or destination, or more particularly the identity of the person represented by the TO:, FROM: or CC: field of an e-mail address or the abstraction of an IP address). Thus, we apply rigorous training and technological advancements to combine both our automated and manual (human) processes to characterize communications – ensuring protection of the privacy rights of the American people. This is not just our judgment, but that of the relevant inspectors general, who have also reported this.”
In other words, Americans are absolutely the target of billions of monthly intrusions, but said data “mining” is exempted because it is difficult to identify in advance if a US citizen is implicated in any metadata chain.
Only it isn’t as it is the whole premise behind Boundless Informant.
An NSA factsheet about the program, acquired by the Guardian, says: “The tool allows users to select a country on a map and view the metadata volume and select details about the collections against that country.”
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.
The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, “What type of coverage do we have on country X” in “near real-time by asking the SIGINT [signals intelligence] infrastructure.”
Under the heading “Sample use cases”, the factsheet also states the tool shows information including: “How many records (and what type) are collected against a particular country.”
A snapshot of the Boundless Informant data, contained in a top secret NSA “global heat map” seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.
Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. Jordan, one of America’s closest Arab allies, came third with 12.7bn, Egypt fourth with 7.6bn and India fifth with 6.3bn.
Next up: more NSA lies of course.
The disclosure of the internal Boundless Informant system comes amid a struggle between the NSA and its overseers in the Senate over whether it can track the intelligence it collects on American communications. The NSA’s position is that it is not technologically feasible to do so.
At a hearing of the Senate intelligence committee In March this year, Democratic senator Ron Wyden asked James Clapper, the director of national intelligence: “Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?”
“No sir,” replied Clapper.
Judith Emmel, an NSA spokeswoman, told the Guardian in a response to the latest disclosures: “NSA has consistently reported – including to Congress – that we do not have the ability to determine with certainty the identity or location of all communicants within a given communication. That remains the case.”
Other documents seen by the Guardian further demonstrate that the NSA does in fact break down its surveillance intercepts which could allow the agency to determine how many of them are from the US. The level of detail includes individual IP addresses.
IP address is not a perfect proxy for someone’s physical location but it is rather close, said Chris Soghoian, the principal technologist with the Speech Privacy and Technology Project of the American Civil Liberties Union. “If you don’t take steps to hide it, the IP address provided by your internet provider will certainly tell you what country, state and, typically, city you are in,” Soghoian said.
…
At a congressional hearing in March last year, Alexander denied point-blank that the agency had the figures on how many Americans had their electronic communications collected or reviewed. Asked if he had the capability to get them, Alexander said: “No. No. We do not have the technical insights in the United States.” He added that “nor do we do have the equipment in the United States to actually collect that kind of information”.
Turns out they do, and that perjury in the US is now merely another facet of the “New Normal.” Plus what difference does it make that yet another member of the most transparent administration perjured themselves. Then again, when the head of the Department of Justice is being investigated for lying to Congress under oath, one can only laugh.
That laughter risks becoming an imbecilic cackle when reading the following veiled threat to the Guardian from the NSA’s Judith Emmel: “The continued publication of these allegations about highly classified issues, and other information taken out of context, makes it impossible to conduct a reasonable discussion on the merits of these programs.”
In other words, the best discussion is one that would simply not take place as reporters should promptly stop actually reporting, and fall back to their New Normal role of being access journalists to important people (see Andrew Ross Sorkin’s rise to fame on… nothing) with zero critical insight or investigative effort. Or else…

Author of the Patriot Act spoke out today, says this is in direct violation of the act. Here is the link.
http://www.guardian.co.uk/commentisfree/2013/jun/09/abuse-patriot-act-must-end?guni=Network front:network-front full-width-1 bento-box:Bento box:Position2
When I worked for Verizon back in the 90’s we knew that Cell towers got signals that contained (Metadata) which gave the tower ID#, Cell ESN#, caller number, receiving number, receiving cell tower(S) receiving ESN, duration, roaming information. Just to start! So if he is saying we are not listening to you, that Technically may be right, BUT I doubt it……Wiretaps intercept Cell#s with Number, ESN so that data CAN be used to TAP any phone on the grid. Data mining from phone providers is common typically they use it for marketing to get more money for ads. In the late 90’s I worked for a computer company that had a contract to build a VERY high tech system in Raleigh NC that “Data Mined” MILLIONS of records from various “Search Engine” web sites like “Google”, there were very highly skilled researchers working on how to mine the most records in the shortest time giving the desired “Results”. One Monday we were told that the “Company” had to fold due to lack of funding! We did not have a “Direct” connection to the search providers but we DID have a FTP connection to grab all the data over very fast connections! So, my question now is did this country really go belly up? Or was it just a test platform for projects like “PRISM” BTW, that was the name also of this system!
Now cell phones are equiped with built in GPS tracking, so the Metadata should also have that embeded into it! So, they Know where you are If it is turned on.