And what could possibly go wrong?
– The Cyber Wars Begin: Obama Says US “Must Retaliate” Against China For Historic Data Breach (ZeroHedge, Aug 1, 2015):
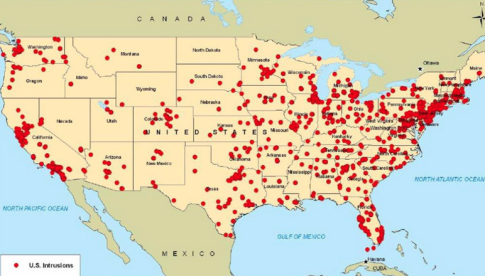
On Friday, we highlighted a “secret” NSA map which purports to show every Chinese cyber attack on US targets over the past five years. “The prizes that China pilfered during its ‘intrusions’ included everything from specifications for hybrid cars to formulas for pharmaceutical products to details about U.S. military and civilian air traffic control systems,” intelligence sources told NBC, who broke the story.
The release of the map marked the culmination of a cyber attack propaganda campaign which began with accusations that North Korea had attempted to sabotage Sony, reached peak absurdity when Penn State claimed Chinese spies had taken control of the campus engineering department, and turned serious when Washington blamed China for what was deemed “the largest theft of US government data ever.” “Whether all of this is cause for the Pentagon to activate the ‘offensive’ component of its brand new cyber strategy remains to be seen,” we said yesterday.
As it turns out, the Office of Personnel Management breach will indeed be used to justify a cyber “retaliation”against China, because as The New York Times notes, “the hacking attack was so vast in scope and ambition that the usual practices for dealing with traditional espionage cases [do] not apply.” Here’s more:
The Obama administration has determined that it must retaliate against China for the theft of the personal information of more than 20 million Americans from the databases of the Office of Personnel Management, but it is still struggling to decide what it can do without prompting an escalating cyberconflict.
The decision came after the administration concluded that the hacking attack was so vast in scope and ambition that the usual practices for dealing with traditional espionage cases did not apply.
But in a series of classified meetings, officials have struggled to choose among options that range from largely symbolic responses — for example, diplomatic protests or the ouster of known Chinese agents in the United States — to more significant actions that some officials fear could lead to an escalation of the hacking conflict between the two countries.
That does not mean a response will happen anytime soon — or be obvious when it does.
So the US will do something, it just doesn’t yet know what or when or even if anyone will notice, but one thing is clear: “this aggression will not stand, man.”
The problem with “symbolic” responses is that they are merely, well, symbolic, and any real retaliation risks escalating the “cyberconflict.” Then again, not doing anything also risks prompting an escalation:
But over recent days, both James Clapper Jr., the director of national intelligence, and Adm. Michael S. Rogers, director of the National Security Agency and commander of the military’s Cyber Command, have hinted at the internal debate by noting that unless the United States finds a way to respond to the attacks, they are bound to escalate.
Mr. Clapper predicted that the number and sophistication of hacking aimed at the United States would worsen “until such time as we create both the substance and psychology of deterrence.”
This echoes the rhetoric from the DoD’s “cyber strategy” released in April which says that “deterrence is partially a function of perception [and] works by convincing a potential adversary that it will suffer unacceptable costs if it conducts an attack on the United States.”
For now at least, it looks like criminal charges are off the table.
The Justice Department is exploring legal action against Chinese individuals and organizations believed responsible for the personnel office theft, much as it did last summer when five officers of the People’s Liberation Army, part of the Chinese military, were indicted on a charge of the theft of intellectual property from American companies. While Justice officials say that earlier action was a breakthrough, others characterize the punishment as only symbolic: Unless they visit the United States or a friendly nation, none of them are likely to ever see the inside of an American courtroom.
“Criminal charges appear to be unlikely in the case of the O.P.M. breach,” a study of the Office of Personnel Management breach published by the Congressional Research Service two weeks ago concluded. “As a matter of policy, the United States has sought to distinguish between cyber intrusions to collect data for national security purposes — to which the United States deems counterintelligence to be an appropriate response — and cyber intrusions to steal data for commercial purposes, to which the United States deems a criminal justice response to be appropriate.“
Instead, the US may look to remove the so called “great firewall” which Beijing uses to censor content it considers to be subversive or otherwise objectionable.
One of the most innovative actions discussed inside the intelligence agencies, according to two officials familiar with the debate, involves finding a way to breach the so-called great firewall, the complex network of censorship and control that the Chinese government keeps in place to suppress dissent inside the country. The idea would be to demonstrate to the Chinese leadership that the one thing they value most — keeping absolute control over the country’s political dialogue — could be at risk if they do not moderate attacks on the United States.
So perhaps there’s a silver lining in all of this: China’s 650 million internet users may, if only for a split second, be free to surf the web without the Politburo filter.
Of course if the US really wanted to do some cyber damage, the Pentagon could hack into China’s National Bureau of Statistics and see what the country’s real GDP figure looks like, and if that doesn’t teach them a lesson, maybe the best option would be to breach China Securities Finance Corporation and hit the “sell” button.
Finally, for those interested to monitor the global cyber war in real time, you can do so via Norsecorp by clicking on the following map.
Evedy corporation that moved MFG to China for the use of slave labor for the last 25+ years had to give the Chinese government all their trade secrets…………that was the price of cheap labor……GE even gave China their power plants and nuclear power data. The craven lack of protection for the amazing technology the US and Europe held ought never to have been allowed.
China doesn’t need to steal the MFG of any corporations. The only thing they might not have are the military data……….That was the only thing lacking. Every vehicle on the road has Chinese copies, sold by Cherry Motors in China……the data was part of the greedy cost for all that cheap labor……The few who balked at the price could MFG elsewhere. This was all covered in depth in the Wall Street Journal before the government shut them down.
So, if they stole anything, they are military secrets……..
China was also the key player after 2010 in establishing electronic currencies in nations all over the globe which allowed participating nations to trade directly with each other using their own currencies, leaving the dollar out…..They worked overtime in making Hugo Chavez’s Sucre a viable alternative replacing the dollar as world reserve currency.
Today, India, Russia, China, Brazil, much of South & Central America, most emerging African nations including South Africa, Australia and Canada now have alternatives to the dollar…….The US dollar is used by the Euro, Japan, Saudi Arabia and the US……most other nations have abandoned the dollar (and the corrupt US leadership) because they no longer trust the US.
After the crash of 2008-2009 which caused entire nations to go bankrupt when nothing was done to repair or fix a thing in the US economy, the world started moving away from the US. Hugo Chavez offered a strong alternative with the Sucre, Russia and China both adopted it in November of 2010, and the US dollar no longer has precedence over other currencies……….This is what they seek to repair, and it won’t work. The US leadership ought never to have allowed the offshoring of millions of jobs and much of the trade secretes………Now, the people pay the price. It is an appalling lack of decency, and there is no way to put the genie back into the bottle.
The next crash is around the corner, and nothing is on the horizon to avoid or suppress it. We have fools in power, and we face the end of the greatest way of living for mankind.
Cyber laws…….What rot. As if China will run an hide…………..
We were rich too long, and forgot how valuable our knowledge was to the world…….Greedy guts took over, and now, it is too late.
God help us, nobody else can. For evil to flourish, good men need only do nothing………………..Edmund Burke………