– Remote ATM control: Kaspersky Lab details $1bn online bank heist (EXCLUSIVE) (RT, Feb 16, 2015):
Internet security company Kaspersky Lab says the banking industry could be experiencing “a new era in cybercrime.” The company has been investigating a $1 billion attack on financial institutions by a sophisticated hacking group.
The IT security firm says the hackers from the Carabanak group used a complex virus system which was later named after them. It is not like the simple Trojan horse malware used to by-pass security systems, but something much more complex and unique, according to documents exclusively seen by RT.
Russian cyber-security company Kaspersky Lab was invited to look into the matter, after an ATM in the Ukrainian capital Kiev started giving out cash randomly without anyone inserting a card or touching any buttons in late 2013.
The attackers did not look to exploit weaknesses in the company’s software. Instead, they took screenshots of computers at 20-second intervals and were able to learn the victims’ internal procedures. They were then able to copy these and impersonate the victim in order to process fraudulent transactions.
How hackers stole $1billion from the banks #Carbanak#TheSAS2015 – http://t.co/3Dn53l0D5Vpic.twitter.com/LL5YwogpbB
— KasperskyUK (@kasperskyuk) February 16, 2015
Anton Shingarev, Chief of Staff at Kaspersky Lab, said the complex nature of the malware used was unprecedented and it was “the most highly sophisticated criminal attack we have ever seen.”
He added that the cyber-criminals used methods that were used by governments in the past, while each attack took approximately two months and around 10 criminals were working on a daily basis on it.
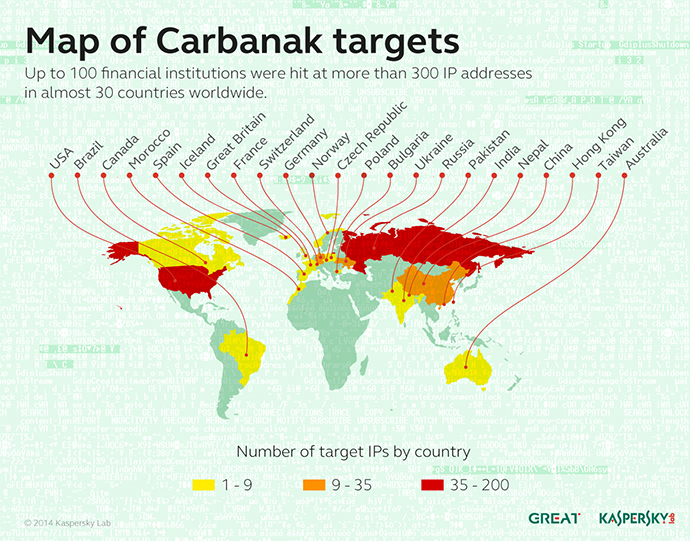
Kaspersky Lab said that most of the victims were located in Russia, the US, Germany, China and Ukraine. The hacking group targeted 30 banks. One customer lost in the region of $7.3 million because of ATM fraud, while another had $10 million stolen due to hackers entering the person’s online banking page.
The money would then be sent to accounts set up mainly in the US and China.
“They managed to get access to the whole banking system. They managed to remotely control ATM’s and they managed to transfer money from one account to another. Due to the extreme level of complexity, banks did not realize they were coming under attack,” Shingarev told RT.
Worryingly, the criminals were able to bypass advanced control and fraud detection systems, which the financial industry has been reliant on for years for internet security. The hackers went down another route to avoid these security systems by using industry-wide funds transfers (the SWIFT network), which would allow them to update the balances of those holding an account in the bank.
For example, the hackers could alter the data for an account that held $1,000 and add extra funds to make the balance $10,000. The criminals would then withdraw $9,000 bringing the balance back to $1,000. As the customer lost no money, he or she would be none the wiser and not raise any alarm.
The attackers were also not too greedy deliberately limiting the amount stolen from each victim to $10 million. This was to ensure that red flags were not raised and law enforcement agencies did not carry out a thorough investigation.
Kaspersky Lab says that little is known about the criminals, as they have now been detected and the IT security firm cannot reveal any details on them. They did mention that the criminals had been working for around two years and they did leave traces which Kaspersky Lab is now studying.
“It’s like an arms race. Security companies develop better protection and criminals develop better malware to bypass it,” Shingarev added.
The Carbanak malware used by the cyber-criminals proved to be very successful in helping the attackers steal around $1 billion. Kaspersky Lab is worried about the increasing sophistication of attacks.
“Despite increased awareness of cybercrime within the financial services sector, it appears that spear phishing attacks and the old exploits (for which patches have been disseminated) remain effective against larger companies. Attackers always use this minimal effort approach in order to bypass a victim ?s defenses,” a press release from the company stated.

Why is this story making headlines now? So that they can get the excuse to censor the web. I am not surprised at the story, the timing, or any of it. They want to destroy the alternative news outlets…….believe me.
Stealing from the banks……it is a drop in the bucket for those crooks…….and this story is being used to fool the people again.
Once upon a time when a person put his money in the bank, and it was there any time he wanted it, that was different. But, they keep no money on deposit.
Does anyone else remember the story three years ago? When the head of the IMF wanted banks to hold five cents on deposit for every dollar of asset they claimed?
The banks would have had to borrow the five cents.
The idea was tabled, and never brought up again.
What a sham.
Does calling this 7.0 quake just to hit the Japan coast an “aftershock” make sense to you? Comparing it to the 3/11 quake, they are now calling it an aftershock. What rubbish is this? They are evacuating towns, awaiting a Tsunami and calling it an aftershock….
http://enenews.com/quake-magnitude-7-hits-northeast-japan-strongest-hit-country-2013-felt-along-entire-pacific-coastline-1000-km-followed-multiple-aftershocks-one-centered-japan-trench-official-event-related
Because Kaspersky’s Anti Virus has detected the NSA’s “back door” intrusion virus installed on all PC’s and Apple computers, and is the ONLY one to do it, the CIA/FBI have instructed government quangos to not use Kaspersky, claiming it is a hacking tool for Russia, which it isn’t.
Cue, Wikileaks to clear things up.
https://www.rt.com/news/409376-cia-wrote-code-to-impersonate-kaspersky/