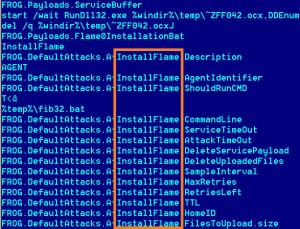
– US government developing ultimate cyber weapon; Prime-factoring quantum computing makes encryption obsolete (Natural News, Aug 20, 2012)
The U.S. government is making steady progress on a game-changing technology that would give it the most powerful weapon ever devised in the realm of cyber warfare and information dominance. The weapon is called a “prime-factoring quantum computer,” and a small-scale version of the game-changing technology has already been demonstrated by researchers at UC Santa Barbara, where qubits — quantum bits of computational potential — factored the number 15 into its prime factors three and five.
So what, you say? Can’t any fifth grader do the same thing?
But hold on: Every digital encryption algorithm used today depends in the extreme mathematical difficulty of factoring (the prime numbers of) very large numbers. When you buy something on the internet, for example, your credit card number is sent to the merchant using something called “SSL encryption” which typically uses a 40-bit, 128-bit or sometimes even a 256-bit encryption algorithm. Anyone who might intercept your web form data would not be able to extract your credit card number unless they decrypted your encrypted data. This task requires extraordinary computing power.
For example, using “military grade” 512-bit encryption means that it would take a supercomputer longer than the age of the known universe to decrypt your file and expose your secrets. This is why the U.S. military uses such encryption. It’s virtually unbreakable given today’s computers.
But quantum computers have the spooky ability to process complex decryption algorithms using what some scientists believe are computational bits which coexist in an infinite number of parallel universes. You feed the quantum computer a decryption task, and it “calculates” the answer in all possible parallel universes. The correct answer then emerges in this universe, seemingly magically.
Quantum computing appears to break the laws of physics… yeah, it’s spooky
Read moreUS Government Develops Ultimate Cyber Weapon; Prime-Factoring Quantum Computing Makes Encryption Obsolete



 that the massive piece of malware, which collected critical intelligence information from Iran, was created with the aim of slowing the country’s suspected nuclear weapon development.
that the massive piece of malware, which collected critical intelligence information from Iran, was created with the aim of slowing the country’s suspected nuclear weapon development.